Try Hack Me
Try Hack Me is a premier learning platform that offers a wealth of resources for cybersecurity enthusiasts and professionals alike.
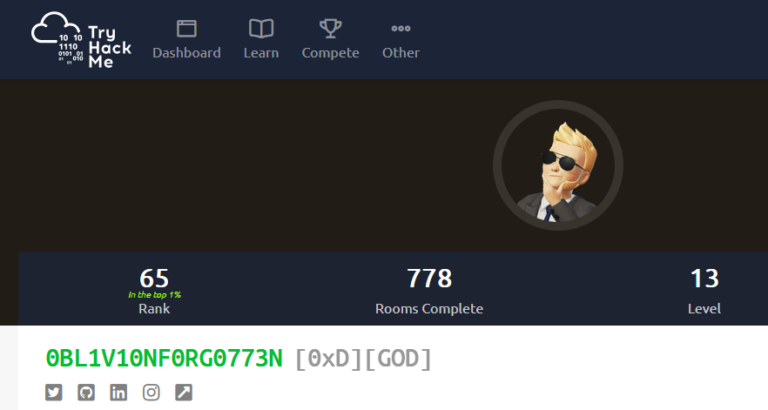
My Profile
You can view my profile on Try Hack Me. On THM, you can explore the Leaderboards: King of the Hill (KOTH). Additionally, enhance your skills by diving into Hacktivities: Practice and resources are also available in the Resources NewsRoom.
Profile URL:
I have achieved full mastery on THM, reaching level 13 and earning the title: 0BL1V10NF0RG0773N [0xD] [G0D], currently holding [CYBER CRUSADER] because an event.
Ranked in the Top 46
If you require assistance, advice, or tips, please feel free to reach out through my social media channels. I'm always happy to help fellow learners and professionals in the cybersecurity field.
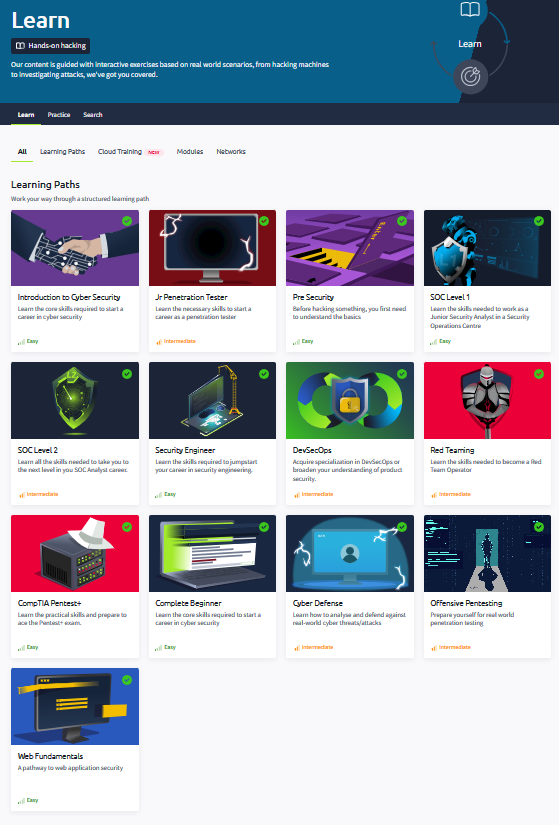
Explore All Pathways by Clicking Here!
Important Note: Please be aware that the dates shown in the slideshows for certification achievements do not always reflect the actual dates I obtained them. While the download dates are consistent, the true achievement dates may vary. Thank you for your understanding.
I have earned the following certifications:
- Introduction to Cyber Security
Learn the core skills required to start a career in cyber security.- Learn about different careers in cyber
- Hack your first application
- Defend against a live cyber attack
- Explore security topics in the industry
- Junior Penetration Tester
Learn the necessary skills to start a career as a penetration tester.- Pentesting methodologies and tactics
- Enumeration, exploitation, and reporting
- Realistic hands-on hacking exercises
- Learn security tools used in the industry
- Pre Security
Before hacking something, you first need to understand the basics.- Cyber security basics
- Networking basics and weaknesses
- The web and common attacks
- Learn to use the Linux operating system
- SOC Level 1
Learn the skills needed to work as a Junior Security Analyst in a SOC.- Detect and analyse traffic anomalies
- Monitor endpoints for threats
- Utilise SIEM tools to handle incidents
- Investigate forensic artefacts
- SOC Level 2
Learn all the skills needed to advance your SOC Analyst career.- Security operations
- Introductory incident response
- Malware analysis
- Threat hunting and emulation
- Security Engineer
Learn the skills required to jumpstart your career in security engineering.- Network security engineering
- System security engineering
- Software security engineering
- Risk management & incident response
- DevSecOps
Specialize in DevSecOps or broaden your understanding of product security.- Hands-on CI/CD Pipeline Security
- Introduction to Securing IaC
- Containerisation Security
- Applications of DevSecOps Frameworks
- Red Teaming
Learn the skills needed to become a Red Team Operator.- Use diverse techniques for initial access
- Enumerate and persist on targets
- Evade security solutions
- Exploit Active Directory
- CompTIA Pentest+
Learn practical skills and prepare to ace the Pentest+ exam.- Hands-on exercises aligning to PenTest+ exam objectives
- Practical exam preparation for Performance Based Questions
- Complete Beginner
Learn the core skills required to start a career in cyber security.- Web application security
- Network security
- Basic Linux
- Scripting
- Web Fundamentals
A pathway to web application security.- Understand web fundamentals
- Major vulnerabilities explained
- Learn industry-used tools
- Web application assessments
- Cyber Defense
Learn how to analyze and defend against real-world cyber threats/attacks.- Detect threats
- Gather threat actor intelligence
- Understand and emulate adversary TTPs
- Identify and respond to incidents
- Offensive Pentesting
Prepare yourself for real-world penetration testing.- Utilize industry-standard tools
- Learn realistic attack scenarios
- Train in offensive security
- Supporting exercises & resources
Introduction to Cyber Security

Synopsis:
I am pleased to announce that on November 3, 2024, I was awarded a certificate in Introduction to Cyber Security by TryHackMe. This certification validates my comprehensive understanding of fundamental concepts and practices in cybersecurity. Throughout this course, I explored a wide range of cybersecurity topics, gaining insights into common risks, countermeasures, and ethical considerations crucial to the field. The hands-on exercises and labs provided practical experience, allowing me to effectively apply cybersecurity principles in real-world scenarios.
Important Takeaways:
- Comprehensive Understanding: Built a solid foundation in the fundamentals of cybersecurity, including risk assessment, incident response procedures, and threat landscape analysis.
- Threat Awareness and Mitigation: Gained knowledge of common cybersecurity threats, such as phishing, malware, and social engineering, along with practical countermeasures to mitigate these risks.
- Ethical and Legal Framework: Explored the ethical and legal aspects of cybersecurity, focusing on privacy, compliance, and ethical hacking practices.
- Practical Application: Mastered the use of various cybersecurity tools and techniques through interactive labs, enhancing my skills in security monitoring, penetration testing, and vulnerability scanning.
- Real-World Experience: Applied cybersecurity concepts in real-world scenarios, strengthening my ability to protect digital assets and respond effectively to security incidents.
Advantages and Dedication:
Earning this credential empowers me to actively safeguard data and digital assets against the ever-evolving landscape of cyber threats. I am dedicated to staying at the forefront of cybersecurity by continuously refining my skills and staying informed of the latest advancements, enabling me to anticipate and address emerging security challenges.
Junior Penetration Tester

Synopsis:
I am proud to have earned the Junior Penetration Tester certification from TryHackMe on November 3, 2024. This credential validates my foundational skills and real-world experience in the dynamic field of penetration testing. Through focused training and practical application, I have honed the abilities needed to identify, exploit, and mitigate security vulnerabilities in digital systems and networks.
Important Takeaways:
- Proficiency in Penetration Testing: Developed advanced skills in conducting penetration tests to evaluate and enhance the security posture of networks and systems.
- Methodologies and Tools: Acquired knowledge of various penetration testing methodologies, tools, and techniques, including reconnaissance, exploitation, and post-exploitation phases.
- Vulnerability Identification: Demonstrated expertise in identifying and exploiting common security weaknesses, such as software bugs, misconfigurations, and weak authentication systems.
- Ethical and Legal Considerations: Gained a deep understanding of the ethical and legal implications of penetration testing, ensuring adherence to responsible and compliant practices.
- Report Generation: Mastered the ability to generate detailed reports outlining discovered vulnerabilities and providing actionable recommendations for remediation.
Advantages and Dedication:
As a certified Junior Penetration Tester, I am equipped to assist organizations in proactively detecting and addressing security vulnerabilities, reducing the risks of cyberattacks. By prioritizing both security and compliance in my testing services, I remain committed to ethical practices and continuous learning, staying at the forefront of cybersecurity standards.
Pre Security

Synopsis:
I am pleased to report that on November 3, 2024, I received my Pre Security certificate from TryHackMe.
This certification attests to my mastery of the fundamental concepts required to comprehend and implement efficient security
protocols in digital environments. Through this course, I have gained valuable insights into threat modeling, risk assessment
methods, and pre-security measures, laying a solid foundation for developing robust cybersecurity protocols.
Important Takeaways:
- Fundamental Pre-Security Concepts: Developed a solid understanding of pre-security
principles and guidelines, essential for implementing proactive security measures. - Threat Modeling and Risk Assessment: Learned techniques for risk assessment and
threat modeling, enabling the identification and prioritization of security risks. - Identification of Security Hazards: Proven ability to recognize and rank security
hazards, facilitating the development of preemptive security measures. - Proactive Security Strategies: Acquired practical experience in implementing pre-security
measures to strengthen overall security posture and effectively mitigate risks.
Advantages and Dedication:
With the certificate I obtained, I am now equipped to contribute effectively to the development and implementation of security policies
that protect digital assets and proactively mitigate cybersecurity risks. My dedication lies in staying abreast of the latest advancements
in security technology and emerging threats. I am committed to fostering organizational resilience against cyber threats through continuous
learning and adaptation.
SOC Level 1

Synopsis:
I am proud to have achieved the Junior Security Analyst (SOC Level 1) certification, demonstrating proficiency in fundamental cybersecurity operations critical for safeguarding organizations against evolving threats. This certification highlights my role as a Triage Specialist, specializing in monitoring, investigating, and responding to security alerts to bolster overall security posture.
Important Takeaways:
- Effective Alert Triage: Developed proficiency in monitoring and investigating security alerts within a dynamic 24×7 SOC operations environment, ensuring prompt identification and response to potential threats.
- Security Tool Management: Acquired skills in configuring and managing security tools to optimize threat detection and incident response capabilities, leveraging technology for enhanced security operations.
- IDS Signature Development: Demonstrated ability to develop and implement Intrusion Detection System (IDS) signatures, improving the detection and mitigation of malicious activities across network environments.
- Incident Escalation Protocols: Enhanced understanding of incident escalation procedures, enabling effective communication and collaboration with Tier 2 analysts and Team Leads to address critical security threats.
Advantages and Dedication:
As a certified Junior Security Analyst, I am equipped with foundational skills essential for contributing effectively to cybersecurity operations. In my role as a Triage Specialist, I am committed to proactive monitoring and rapid response, safeguarding critical assets and infrastructure against cyber threats to ensure organizational resilience and security.
SOC Level 2

Synopsis:
I am proud to have achieved the Junior Security Analyst (SOC Level 2) certification, demonstrating advanced proficiency in cybersecurity operations critical for safeguarding organizations against sophisticated threats. This certification highlights my role as a seasoned Triage Specialist, specializing in advanced monitoring, investigation, and response techniques to enhance overall security posture.
Important Takeaways:
- Advanced Alert Triage and Analysis: Developed advanced proficiency in monitoring and analyzing security alerts within a dynamic 24×7 SOC operations environment, enabling rapid identification and response to complex threats.
- Advanced Security Tool Management: Mastered the configuration and management of advanced security tools to optimize threat detection and incident response capabilities, leveraging technology for proactive security operations.
- In-depth IDS Signature Development: Demonstrated expertise in developing and implementing intricate Intrusion Detection System (IDS) signatures, enhancing the detection and mitigation of sophisticated malicious activities across network environments.
- Advanced Incident Handling and Escalation Protocols: Enhanced understanding of advanced incident handling and escalation procedures, facilitating seamless communication and collaboration with Tier 2 analysts and Team Leads to address critical security threats effectively.
Advantages and Dedication:
As a certified Junior Security Analyst (SOC Level 2), I am equipped with advanced skills essential for leading cybersecurity operations. In my role as a seasoned Triage Specialist, I am committed to proactive monitoring, advanced threat response, and collaboration to safeguard critical assets and infrastructure against sophisticated cyber threats. My dedication to continuous learning and improvement ensures that I stay ahead of emerging threats and contribute effectively to organizational security and resilience.
Security Engineer
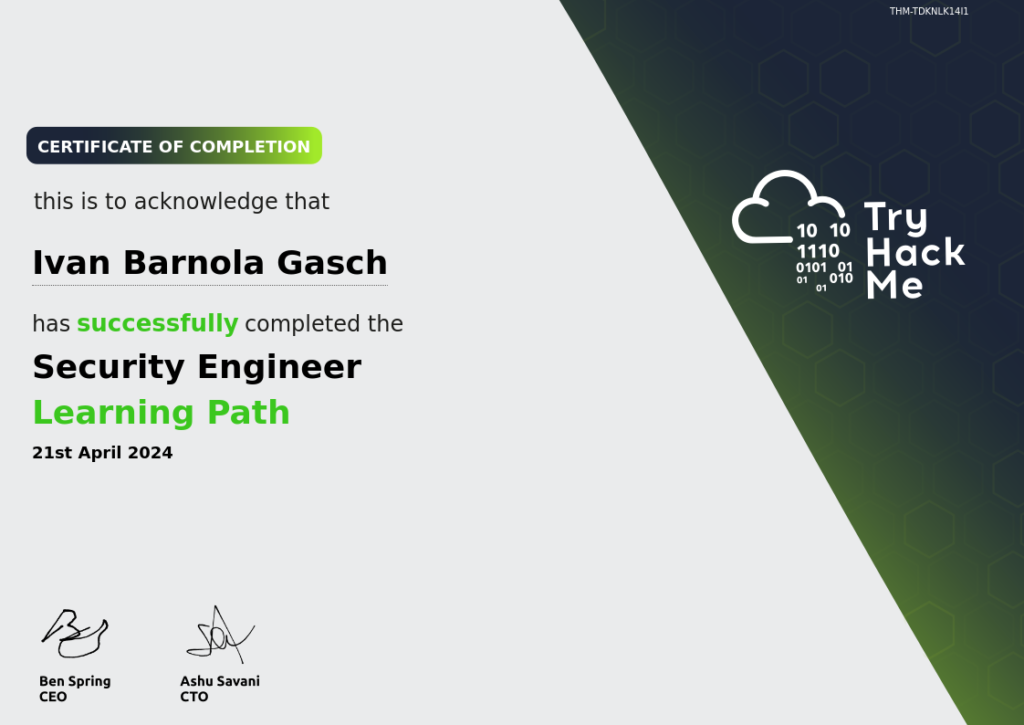
Synopsis:
I am honored to have earned the Security Engineer certificate, validating my expertise and proficiency in designing, implementing, and maintaining robust cybersecurity solutions. This certification recognizes my role as a Security Engineer, responsible for developing and executing security strategies to protect organizations from evolving cyber threats.
Important Takeaways:
- Advanced Cybersecurity Architecture Design: Developed expertise in designing and implementing comprehensive cybersecurity architectures tailored to organizational needs, incorporating defense-in-depth principles.
- Security Tool Implementation and Management: Mastered the implementation and management of security tools and technologies to enhance threat detection, incident response, and overall security posture.
- Vulnerability Assessment and Penetration Testing (VAPT): Acquired skills in conducting thorough vulnerability assessments and penetration tests to identify and remediate security weaknesses proactively.
- Incident Response and Recovery: Gained proficiency in incident response procedures, including containment, eradication, and recovery, to minimize the impact of cybersecurity incidents.
- Security Compliance and Governance: Enhanced understanding of security compliance frameworks and governance standards, ensuring adherence to regulatory requirements and industry best practices.
Advantages and Dedication:
Earning the Security Engineer certificate signifies my dedication to excellence in cybersecurity engineering. As a Security Engineer, I am committed to leveraging my expertise to design and implement robust cybersecurity solutions that protect organizations’ critical assets and infrastructure. I remain proactive in staying updated with emerging threats and technologies to continuously enhance cybersecurity defenses and resilience.
DevSecOps

Synopsis:
I am thrilled to have earned the DevSecOps certificate, showcasing my proficiency in integrating security practices into the DevOps lifecycle to ensure secure and efficient software development processes. This certification acknowledges my role as a DevSecOps practitioner, responsible for bridging the gap between development, operations, and security teams to prioritize security throughout the software development lifecycle.
Important Takeaways:
- Security Integration in DevOps Processes: Developed expertise in integrating security practices, including vulnerability scanning, secure coding, and automated testing, into continuous integration and deployment pipelines.
- Secure Infrastructure as Code (IaC): Mastered the implementation of secure Infrastructure as Code (IaC) practices, leveraging tools like Terraform and CloudFormation to provision and manage cloud resources securely.
- Container Security: Acquired skills in securing containerized environments using best practices for Docker and Kubernetes, ensuring the integrity and confidentiality of containerized applications.
- Security Automation and Orchestration: Learned to automate security processes and orchestrate security tooling within DevOps workflows to achieve continuous security monitoring and incident response.
- Collaborative Security Culture: Fostered a collaborative security culture by promoting cross-functional collaboration between development, operations, and security teams to embed security into every stage of the development lifecycle.
Advantages and Dedication:
Earning the DevSecOps certificate signifies my commitment to advancing secure DevOps practices. As a DevSecOps practitioner, I am dedicated to implementing security as code, fostering a culture of collaboration, and ensuring the delivery of secure and resilient software solutions. I remain proactive in staying abreast of emerging technologies and best practices to drive continuous improvement in DevSecOps processes and elevate organizational security.
Red Teaming

Synopsis:
I am thrilled to have completed the Red Teaming pathway, acquiring advanced skills in emulating potential adversary attacks and conducting successful Red Team engagements to enhance defense capabilities in complex environments. This certification reflects my ability to challenge and strengthen the defense posture of organizations through strategic offensive security practices.
Important Takeaways:
- Adversary Emulation Mastery: Developed expertise in emulating potential adversary attacks beyond standard penetration testing, simulating sophisticated scenarios to assess and enhance defense readiness.
- Comprehensive Red Team Engagements: Acquired skills to conduct successful Red Team engagements, evaluating and bolstering clients’ defense strategies against evolving cyber threats.
- Strategic Defense Challenge: Enhanced capability to challenge defense capabilities, identifying weaknesses and recommending proactive measures to fortify security posture.
Advantages and Dedication:
By completing the Red Teaming pathway, I am positioned for significant career advancement in offensive security roles. This certification opens doors to strategic positions in cybersecurity, empowering me to contribute effectively to organizational defense strategies against sophisticated cyber threats.
I am committed to applying the expertise gained from this pathway to enhance cybersecurity initiatives. My goal is to ensure organizations are well-prepared to defend against evolving threats, embodying a proactive approach to cybersecurity excellence.
CompTIA Pentest+

Synopsis:
I am delighted to have completed the CompTIA PenTest+ pathway, gaining practical skills and knowledge essential for penetration testing and vulnerability management in cybersecurity.
Important Takeaways:
- Proficiency with Penetration Testing Tools: Mastered industry-standard penetration testing tools to assess and evaluate network security effectively.
- Network Services Exploitation: Acquired the ability to identify and exploit various network services to uncover vulnerabilities and weaknesses.
- Web Application Security: Developed skills in identifying and exploiting common vulnerabilities in web applications to enhance security measures.
- Windows Active Directory Security: Enhanced understanding of Windows Active Directory and techniques for attacking Kerberos authentication systems.
- Post-Exploitation Techniques: Gained knowledge of post-exploitation techniques using tools like Powerview, Bloodhound, and Mimikatz to assess and mitigate security risks.
Advantages and Dedication:
Completion of this pathway prepares individuals to pursue the CompTIA PenTest+ certification, validating expertise in penetration testing methodologies and techniques. I am committed to leveraging these skills to actively contribute to cybersecurity initiatives and stay updated with emerging trends to address evolving security challenges proactively.
Complete Beginner

Synopsis:
I’m proud to have earned the Complete Beginner certificate from TryHackMe on 12/03/2024. This certificate validates my entry-level proficiency in cybersecurity fundamentals. Through this course, I gained foundational knowledge and practical skills essential for understanding digital security concepts and best practices.
Important Takeaways:
- Introduction to Basic Cybersecurity Concepts and Terminology: Acquired foundational knowledge of basic cybersecurity concepts and terminology, setting the groundwork for further exploration in the field.
- Understanding of Common Security Threats and Vulnerabilities: Developed an understanding of common security threats and vulnerabilities, essential for identifying and mitigating risks.
- Familiarity with Essential Security Tools and Techniques: Gained familiarity with essential security tools and techniques used in cybersecurity practices.
- Awareness of Ethical and Legal Considerations: Learned about ethical and legal considerations in cybersecurity, emphasizing the importance of responsible security practices.
- Preparation for Further Exploration and Learning: Equipped with the necessary foundation to continue learning and exploring more advanced topics and certifications in cybersecurity.
Advantages and Dedication:
Earning the Complete Beginner certificate marks the beginning of my journey into cybersecurity. This certification demonstrates my commitment to learning and developing foundational skills necessary for addressing cybersecurity challenges effectively. I am excited to continue my learning journey, explore more advanced topics, and pursue further certifications to advance my career in cybersecurity.
Web Fundamentals

Synopsis:
I am delighted to have earned the Web Fundamentals certificate from TryHackMe on 12/03/2024. This certificate validates my understanding of essential concepts and practical skills in web development and cybersecurity. Through comprehensive training and hands-on exercises, I have acquired the knowledge necessary to design, develop, and secure web applications effectively.
Important Takeaways:
- Mastery of Fundamental Web Development Languages and Technologies: Developed expertise in HTML, CSS, and JavaScript, essential for building modern web applications.
- Proficiency in Building Dynamic and Responsive Web Interfaces: Acquired skills to create dynamic and responsive web interfaces that enhance user experience.
- Understanding of Web Application Architecture and Common Frameworks: Gained insights into web application architecture and familiarity with common frameworks, enabling efficient development practices.
- Knowledge of Security Best Practices: Learned security best practices for web development, including input validation, authentication, and secure coding practices.
- Experience in Identifying and Mitigating Web Security Vulnerabilities: Acquired hands-on experience in identifying and mitigating common web security vulnerabilities such as cross-site scripting (XSS) and SQL injection.
Advantages and Dedication:
As a certified Web Fundamentals practitioner, I am equipped to create engaging and secure web applications that meet user needs while prioritizing security. My expertise in web development and cybersecurity enables me to contribute effectively to the development of robust and resilient web solutions that excel in functionality and security.
I am committed to continuously enhancing my skills and staying updated with the latest advancements in web development and cybersecurity. I pledge to apply best practices and industry standards to ensure the highest level of security and user experience in every web application I develop. My goal is to contribute positively to the field and uphold the principles of secure and user-friendly web development throughout my career.
Cyber Defence

Synopsis:
I’m thrilled to have earned the Cyber Defence certificate from TryHackMe on 12/03/2024. This certificate validates my proficiency in cybersecurity defense strategies and techniques. Through this course, I’ve gained valuable insights and practical skills essential for protecting digital assets from cyber threats.
Important Takeaways:
- Advanced Cybersecurity Concepts: Developed a comprehensive understanding of advanced cybersecurity concepts and principles, enabling me to address complex security challenges with confidence.
- Defensive Strategies and Threat Mitigation: Acquired knowledge and skills in employing defensive strategies to mitigate security risks and threats effectively.
- Proficiency in Security Tools and Technologies: Demonstrated proficiency in utilizing cutting-edge security tools and technologies for threat detection and response, enhancing organizational security posture.
- Experience in Incident Handling and Response: Gained practical experience in incident handling and response procedures, ensuring swift and effective responses to cybersecurity incidents.
- Preparation for Real-World Cybersecurity Challenges: Prepared to address complex cybersecurity challenges in real-world environments through practical training and application of acquired skills.
Advantages and Dedication:
Completion of this Cyber Defence certificate signifies my commitment to excellence in safeguarding digital assets and data from evolving cyber threats. I am dedicated to applying my expertise to enhance organizational security and readiness against complex cybersecurity challenges. I remain proactive in continuous learning and adaptation to stay ahead of emerging threats and contribute effectively to cybersecurity initiatives.
Offensive Pentesting

Synopsis:
I’m thrilled to have earned the Offensive Pentesting certificate from TryHackMe on 10/04/2024. This certificate validates my proficiency in offensive security strategies and techniques, equipping me with essential skills to conduct penetration tests and identify vulnerabilities effectively.
Important Takeaways:
- Mastery of Advanced Penetration Testing Methodologies: Acquired expertise in advanced penetration testing techniques, including reconnaissance, exploitation, and post-exploitation tactics.
- Proficiency in Offensive Security Tools and Frameworks: Developed strong proficiency in using offensive security tools and frameworks to identify and mitigate security vulnerabilities proactively.
- Understanding of Malicious Attack Vectors: Enhanced understanding of attack vectors and techniques used by malicious actors, enabling the implementation of proactive defense measures.
- Experience in Comprehensive Security Assessments: Gained hands-on experience in conducting comprehensive security assessments and penetration tests to enhance organizational security posture.
Advantages and Dedication:
Completion of the Offensive Pentesting certificate signifies my commitment to excellence in offensive cybersecurity. I am dedicated to leveraging my advanced skills and knowledge to conduct thorough penetration tests, identify security gaps, and assist organizations in strengthening their defenses against cyber threats. I will remain proactive in continuous learning and adaptation to stay ahead of evolving security challenges.
Proof of Completion
These credentials signify the completion of learning routes, akin to a degree. Although they may not carry the same weight as a traditional degree, I dedicated considerable effort to earning them.
Thank you for taking the time to review this page.
Scroll down for Hack The Box certificates and machines.
Completed rooms